Foreword
Before the starting the event, I had no intentions to place well or fully compete as I was on vacation. ICTF 2024 was the event I needed to get back into CTF competitions, and I had a lot of fun even though I didn't solve much. Below are my writeups in the order I completed them.
base64
Description: yet another base64 decoding challenge
By: Eth007
- I solved this challege by inversing the operations that the script used to create the secret key. My thought process is explained in the comments of the code.
from Crypto.Util.number import *
q = 64
secret_key = [10, 52, 23, 14, 52, 16, 3, 14, 37, 37, 3, 25, 50, 32, 19, 14, 48, 32, 35, 13, 54, 12, 35, 12, 31, 29, 7, 29, 38, 61, 37, 27, 47, 5, 51, 28, 50, 13, 35, 29, 46, 1, 51, 24, 31, 21, 54, 28, 52, 8, 54, 30, 38, 17, 55, 24, 41, 1]
flag_int = 0 # This is the starting initial value.
for x in reversed(secret_key): # Now reversing the sequence and iterating through every number until it become 0.
flag_int = flag_int * q + x
flag = long_to_bytes(flag_int) # Now reversing back to a byte string
print(flag)Flag: ictf{b4se_c0nv3rs1on_ftw_236680982d9e8449}
bom
Description: 楣瑦筴栴瑟楳渷彣桩渳獥
By: Eth007
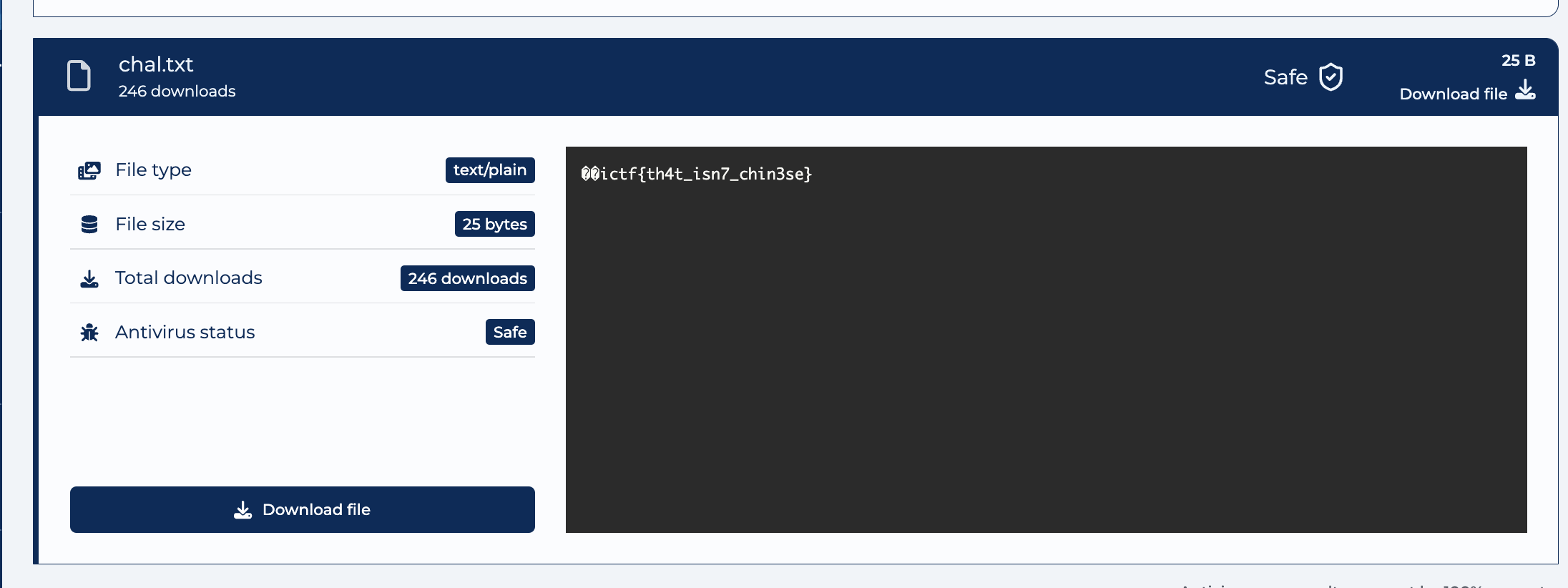
- LOL, the download site solved it for me! But let's see how we can solve this the intended way...
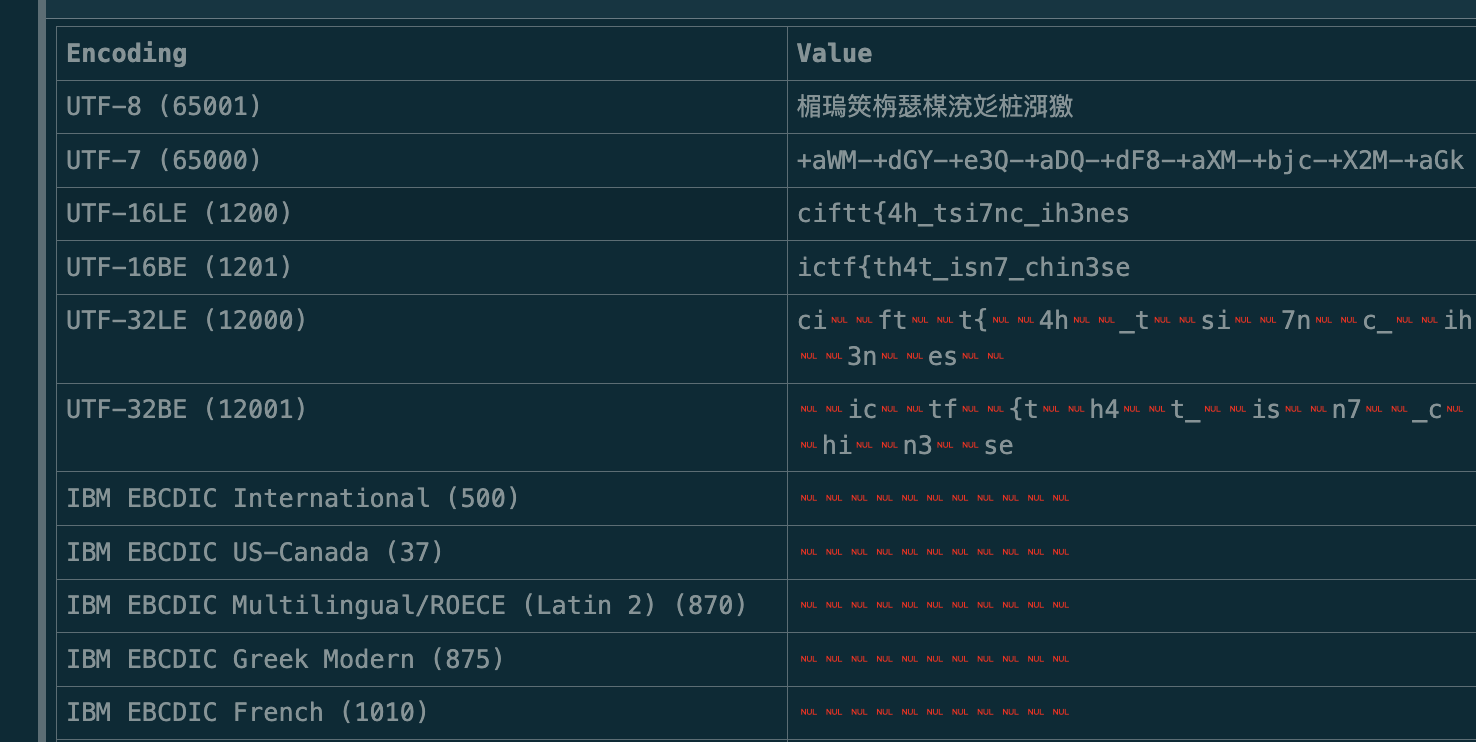
- Fig. 2 shows a much more intended method where we used the CyberChef's Text Encoding Brute Force Tool.
Flag: ictf{th4t_isn7_chin3se}
readme
Description: Try to read the
flag.txtfile.By: maple3142
- Another simple chall, just searching through the source code file allows us to find it and in this case it was in
Dockerfile.
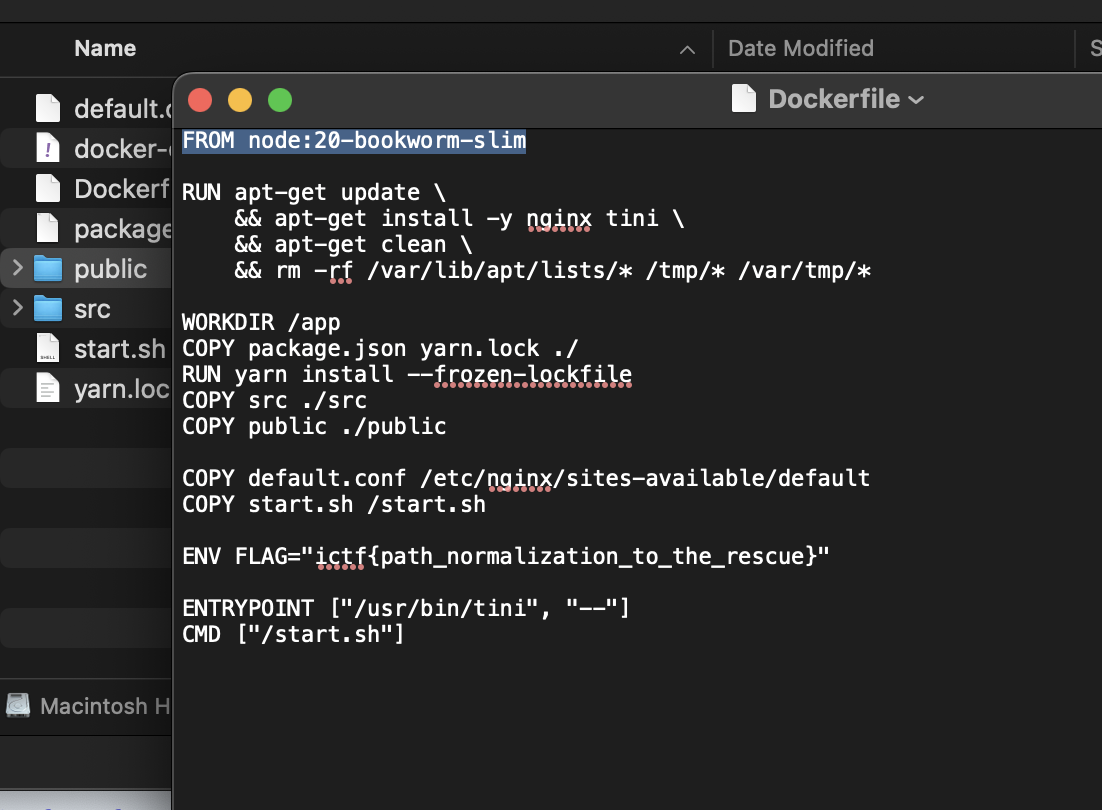
Flag: ictf{path_normalization_to_the_rescue}
cartesian-1
Description: THIS IS AN OSINT CHALLENGE. Greetings. You have been tasked with investigating the whereabouts of a potential recruit. To perform this top-secret background check, we must gather as much information as possible. Please investigate Terrence Descartes. We know that his social accounts are relatively new, so please do not attack anything out of scope. For the sake of this series of challenges, nothing pertaining to Terry has existed before July 17, 2024. Do not investigate anything posted online before then.
By: Eth007
- This was an OSINT challenge, a favorite topic. I started by searching for Instagram pages for people named "Terrence Descartes", I often search Instagram first as it is a common pattern to see other CTFs use IG as part of their OSINT CHallenges.
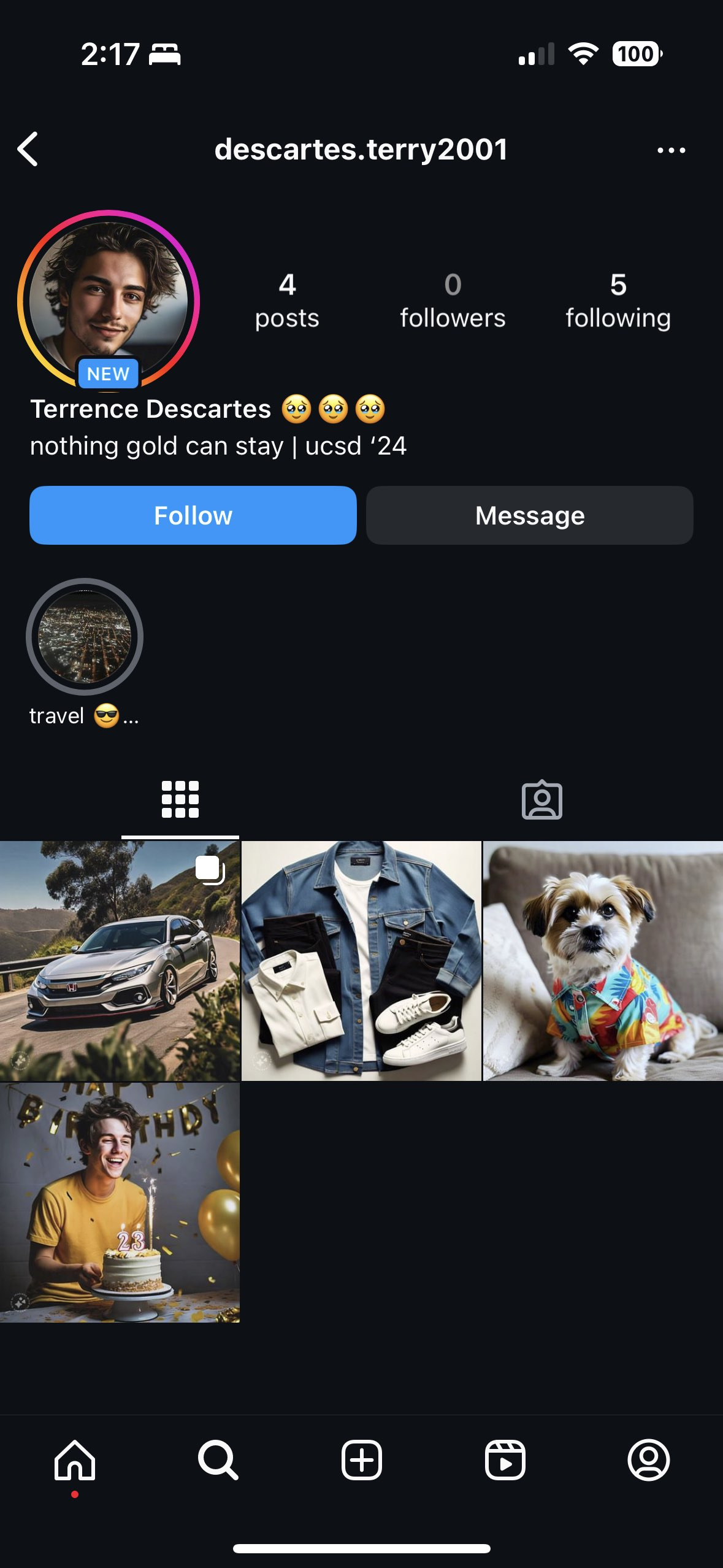
- As seen in Fig. 4, I found a page on Instagram. If we click the "travel😎..." story we find this...
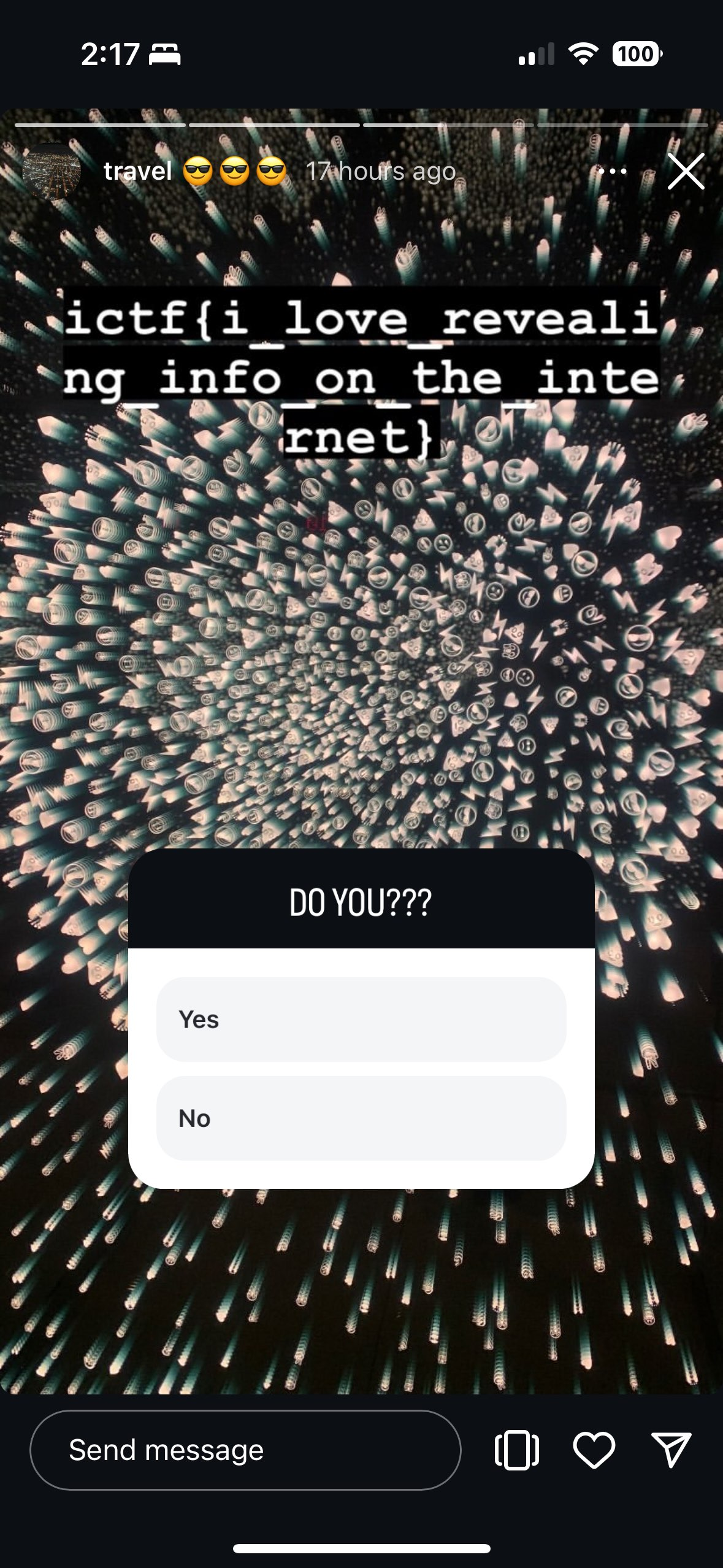
Flag: ictf{i_love_revealing_info_on_the_internet}
unoriginal
Description: i like elf reversing
By: Eth007
- Seems to be a simple Reversing challenge. Let's see what happens when we decompile it with Ghidra...
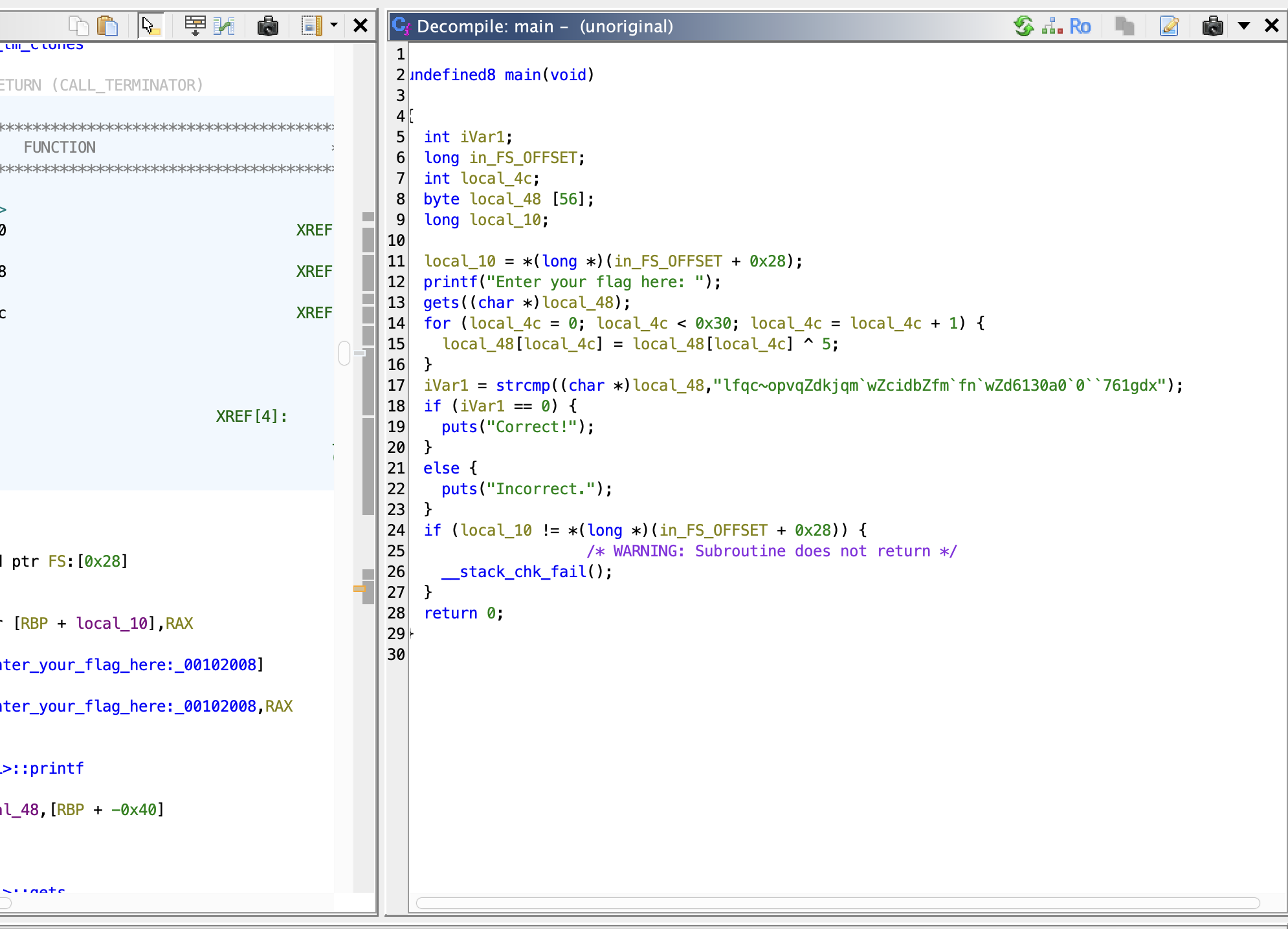
- The code seems to be XORing the string in
iVar1by 5. If we XOR that string by 5, we can get the flag. We can also cross check with the program provided.
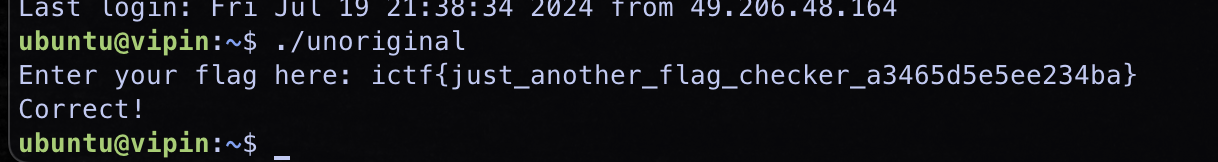
Flag: ictf{just_another_flag_checker_a3465d5e5ee234ba}
Final Words
I had fun solving these simple challenges. I didn't have much time to complete the harder ones but these were fun! TY CTF Admins for a great CTF!